Security and Privacy FAQ
At Katalon Platform, we prioritize providing strong security to ensure your information is safe and easily accessible when needed. We uphold a top-tier security program to safeguard your data by aligning with industry-leading practices and frameworks.
How does the data flow within Katalon systems?
Customer data is exclusively used on Katalon Platform, including Katalon Runtime Engine (KRE), Katalon Studio, Katalon TestCloud, and Katalon TestOps, with no other purposes.
Customer data remains active as long as the account is active. Upon voluntary closure, the data enters an "expired" state, and is subsequently transferred to "cold storage" and retained for 365 days. After this duration, both the account and its associated data are permanently removed from our systems.
What personally identification information (PII) does Katalon retain?
Katalon retains personal identification information (PII) for user license verification, including name, email, and IP address.
We retain PII solely for the purpose of processing license payments; we do not process or manipulate the data in any other way or for any other purposes.
How is user data stored? What encryption is used for data at rest and data in transit?
Data is stored in approved data stores within AWS. Structured data is stored in databases while unstructured data is stored in securely configured AWS S3 buckets.
Data at rest is encrypted with AES 256-bit encryption, while data transit is encrypted with TLS 1.2+ (RSA 2048-bit) encryption. Approved secure channels include SSH, HTTPS, and SFTP.
Sensitive records are hashed SHA256 at the database table level.
How are users' passwords stored?
Users' passwords are stored in secure vault compliant with National Institute of Standards and Technology (NIST) Special Publication 800-63 Digital Identity Guidelines.
Do you have an enforced password policy for administrator accounts? Do you require MFA for administrator accounts?
All administrator accounts are enforced with company-defined length, complexity, and history requirements for passwords. All admin accounts require multi-factor authentication.
Can unprotected user data be accessed by your staff? Is this access audited?
Our internal staff is prohibited from directly accessing user data. Only approved database administrators, upon request from the data owner, are granted access to assist them directly.
All access is meticulously logged and subject to regular audits for accountability and security.
Is there a separation between publicly accessible parts of the application from the data storage?
Yes. Public-facing components are housed in separate logical networks behind load balancers.
Architecture design follows an n-tier pattern with all data decoupled from external-facing application components.
There is no direct external access to data stores.
Does Katalon Platform have cloud providers? Where are they hosted?
Katalon Platform uses Amazon Web Services (AWS) for all production infrastructure and storage. Our AWS location is us-east-1 region (Northern Virginia, USA).
If you need custom data storage location for your organization or project, Katalon Platform offers on-premises and private Software-as-Service (SaaS) solutions. Contact us for more information.
Do you operate physical infrastructure?
Katalon Platform infrastructure is cloud-first, and 100% virtualized. None of our infrastructure is physical.
Does Katalon have an information security program?
Katalon maintains an internal Information Security Management System based on the ISO 27001 and the NIST CyberSecurity Framework. Specifically, it has been assessed and found to conform with ISO/IEC 27001:2022. This program is supervised internally by the Chief Information Security Officer.
All personnel are required to review and provide signed acknowledgement of the policies upon hiring and, at a minimum, annually.
Does Katalon hold any third-party compliance attestations?
Katalon currently holds and maintains SOC2 Type II certification. Katalon is also verified by GDPR Local to ensure compliance with GDPR standards.
Our IT security team also holds the following certifications:
Certified Information Systems Auditor® (CISA®)
Certified Information Security Manager® (CISM®)
Certified in Risk and Information Systems Control® (CRISC®)
Certified Data Privacy Solutions Engineer™ (CDPSE®)
Certified Information Privacy Professional (CIPP)
Certified in the Governance of Enterprise IT® (CGEIT®)
Certified Information Systems Security Professional® (CISSP®)
Information Systems Security Architecture Professional® (ISSAP®)
Project Management Professional® (PMP®)
Offensive Security Certified Professional
Do you have a disaster recovery plan (DRP) and business continuity plan (BCP)?
Katalon systems are hosted in AWS, leveraging AWS services for both continuity and redundancy.
Regular backups and snapshots are taken and tested. Our backup and snapshots are taken daily.Katalon systems are designed with high availability being a primary goal.
How are backups managed? What encryption is used? How are they destroyed when they are no longer needed?
Automated snapshots and backups are captured and destroyed systematically according to policy.
What happens to my data after I stop using Katalon?
Upon a user's request for account deletion or in accordance with our data retention policy, Katalon will delete or return to Customer any Personal Data stored upon request promptly subject to any legal retention obligations, subject to the Customer Terms of Use.
This process is conducted using secure deletion methods that prevent data recovery, ensuring the user's information is permanently removed. Additionally, we regularly audit our data disposal practices to comply with global data protection regulations and industry standards, safeguarding our users' privacy rights.
What is your system patching process/schedule?
Katalon addresses vulnerabilities by prioritizing them according to their critical degree, aligning with our Vulnerability Management policies. Our focus is on making the best effort to address critical, exploitable vulnerabilities identified in externally accessible assets.
Overall, we adopt an immutable image approach for production patching, implementing patches at the "golden image" level to facilitate swift continuous deployment and remediation for production workloads.
Due to architectural design considerations, patch deployment may follow a rolling fashion.
What are some controls you implement for your application security program?
AWS Center for Internet Security (CIS) Benchmark for hardening and vulnerability remediation;
Native Intrusion Detection System (IDS) services enabled at the operating system level;
Vulnerability scanning, workload protection and cloud posture monitoring at the infrastructure level handled via Cloud-Native Application Protection Platform (CNAPP), Cloud Workload Protection Platform (CWPP), and Cloud Security Posture Management (CSPM).
What port does Katalon Studio use to communicate with external resources?
Katalon Studio is a desktop application and establishes connections with Application Lifecycle Management (ALM) integration servers like JIRA, qTest, Slack, and continuous integration (CI). The security protocols for these connections are configured by the users. Specifically, Katalon Studio utilizes port 443 for tasks such as updating, checking bugs, and reporting.
How are configuration and credential data encrypted in Katalon Studio?
App configurations and credential data are encrypted by password-based encryption with Secure Hash Algorithm 1 (SHA1) and Data Encryption Standard in Encrypt-Decrypt-Encrypt multiple encryption mode (PBEWithSHA1AndDESede).
What type of encryption does the 'Encrypt Text' tool in Katalon Studio use?
For Katalon Studio, we use PBEWithSHA1AndDESede algorithm. Katalon Studio keeps a unique salt and secret key to encrypt and de-crypt values when performing the keyword action. We provide only the encryption feature without the decryption feature. Users can only see the encrypted value in the script file. The raw value will not be logged in our report.
You can encrypt text manually by going to Katalon Studio, :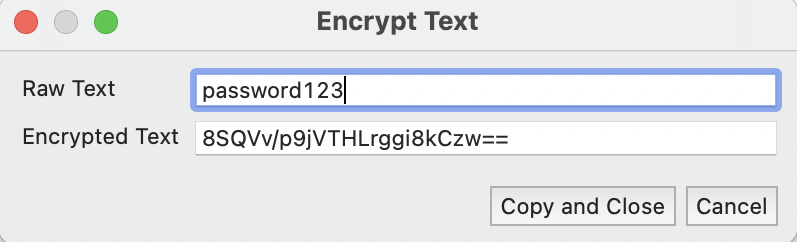 The encrypted value can be used in the following method:
The encrypted value can be used in the following method:
WebUI.setEncryptedText(findTestObject(null), '8SQVv/p9jVTHLrggi8kCzw==')
The method is to fill the encrypted text into a text box for the raw value to be decrypted when running the test.
Do you have separate production and development environments?
Yes. Each of these environments is separated logically, in their Virtual Private Cloud (VPC) server, and has no dependencies on each other.
Are these systems separate from your corporate network?
Yes. Corporate network and Katalon environments are not within the same logical networks.
How do you manage access to production systems?
The principle of least privileged access is enforced to define role-based access to our production systems. All production access requires a secure VPN connection to a management network zone.
No production environments can be accessible publicly (i.e., all 0.0.0.0/0 subnets are shut down).
Also, all production and privileged connections are logged.Describe your coding, testing, and deployment practices.
Katalon employs industry-standard tools and processes to ensure an efficient and secure software delivery lifecycle and CI/CD pipelines.
All development teams follow the Agile methodology with well-defined releases and support cadences.
Code security is reinforced with leading industry tools, enabling static and dynamic code scanning, secured shared secrets, software composition analysis, and vulnerability testing.
Do you perform system vulnerability scans and penetration testing?
We employ AWS Inspector and Nessus for vulnerability scanning. Annual penetration testing is done internally and externally.
Do you perform web application vulnerability testing or intrusion detection?
We perform the following web application vulnerability testing and intrusion detection:
Application vulnerability scans include static, dynamic, and open source dependencies.
AWS CIS Benchmark is used for hardening and vulnerability remediation.
Native IDS services are enabled at the OS level and vulnerability.
Management and tracking are enabled with Amazon Inspector and Nessus.
What type of firewalls/DDOS defense do you use?
Native AWS Web Application Firewall (WAF) services are deployed for edge defense.
How do you monitor your systems and networks?
AWS Security Hub, CloudTrail, GuardDuty, Macie, Prowler, and Wazuh are some of the tools and services we deploy for our network and workload monitoring.
What logging do systems perform? How are they protected?
All cloud workload logs are shipped to a central log management platform where security, compliance, vulnerability logs are performed.
Protection is enabled by regular backups and architecture high availability design.
How does Katalon manage the physical security setup of the system/service (including overview/architecture drawing)?
The Katalon security framework complies with the ISO/IEC 27001 standard for information security management system (ISMS) and covers physical and environmental security to prevent unauthorized physical access, damage, and interference to the organization's information and information processing facilities.
Refer to the following table regarding Katalon's physical and environmental security setup: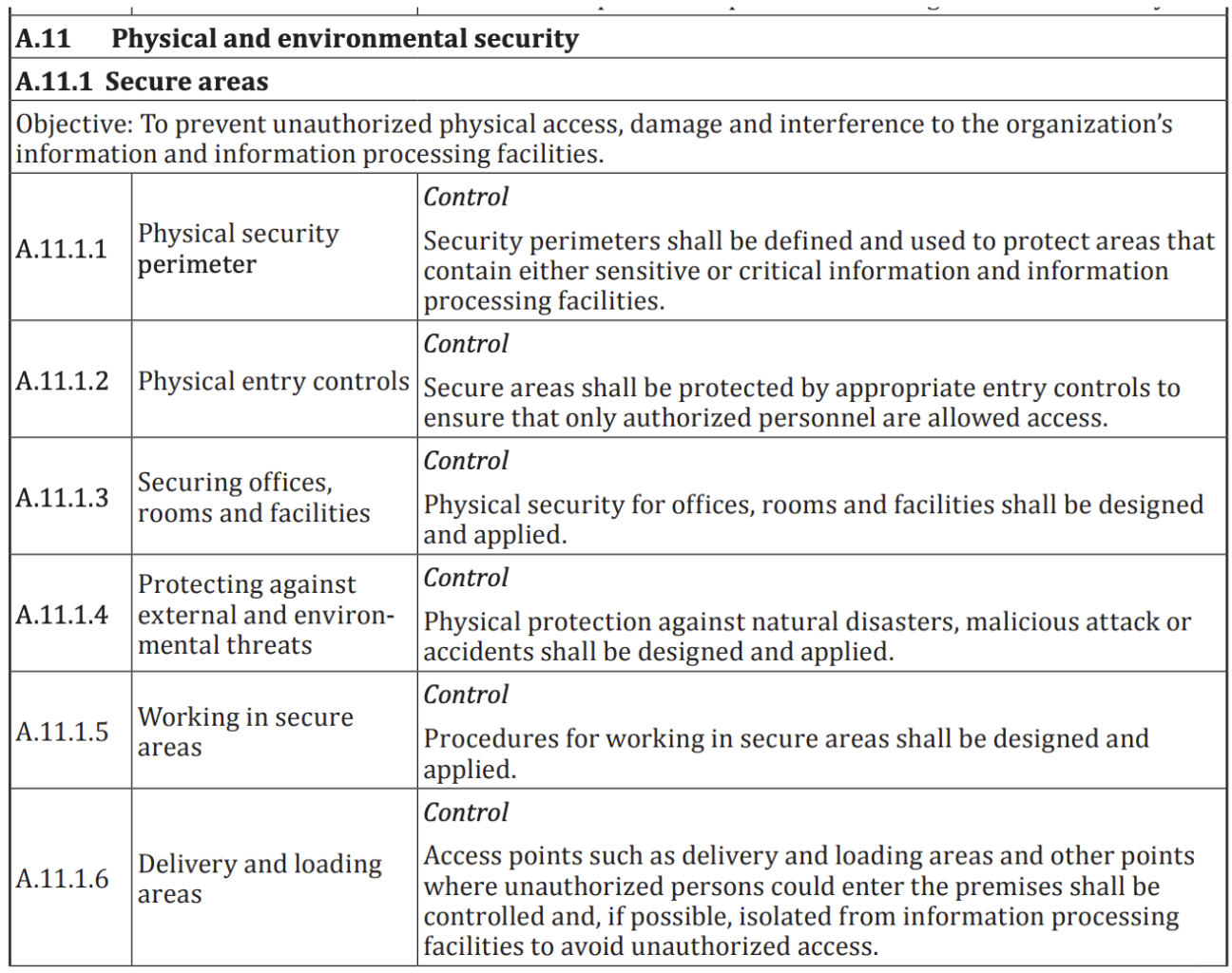
Log4Shell (CVE-2021-44228) - General update
On the 9th of December 2021, a Remote Code Execution exploit CVE-2021-44228 was discovered in a popular Java logging library called Log4j2. It became widespread and known to have been exploited in the wild. This incident was created for further investigation and response to fully understand and respond to the potential attacks on Katalon assets.
Based on our internal review, Katalon Platform users are not affected by this vulnerability.
Katalon TestOps is not affected by this vulnerability. Katalon TestOps uses the default implementation of Spring Boot (implemented Logback through SLF4J for logging). As noted by the Spring Boot team: "Spring Boot users are only affected by this vulnerability if they have switched the default logging system to Log4J2."
Any vulnerability that might exist in Katalon TestOps has been mitigated to some extent in its Web Application Firewall (WAF) controls, which have been updated to block requests embedding known attacks on this vulnerability.
As of 13 December 2021, Katalon TestOps has been upgraded to include Log4J v2.15.0 in its dependencies. In combination with the WAF controls noted above, these corrective actions should completely mitigate any exposure in TestOps.
Katalon Studio Enterprise uses Log4J v1.2.15. This version is not as vulnerable as the version identified in the CVE, particularly given that we are not using the JMSAppender. The similar conclusion is drawn for Katalon Runtime Engine.
For version 8.3.0, you may download it from our GitHub Repo at https://github.com/katalon-studio/katalon-studio/releases/tag/v8.3.0.
We encourage our users to download and use the suggested versions. During your usage, please do let us know of any feedback that you have with the product version.
Does the GPT-powered Manual Test Generator engine employ closed-model AI or open source? Is the data shared or used by any other third party?
- The GPT-powered Katalon Manual Test Cases Generator is based on the cloud API of OpenAI. We only send requests to OpenAI and receive responses from their server. No prompt or answer submitted through Katalon products is used by OpenAI to train models.
- The data is retained by OpenAI for a maximum of 30 days, solely for abuse and misuse monitoring purposes, after which it will be deleted. For more information, see: OpenAI's API data usage policy.
- Katalon also does not store prompts and answers submitted through the Manual Test Generator.